Featured
Table of Contents
- – Openvpn(8): Secure Ip Tunnel Daemon - Linux Man...
- – What Is Openvpn? - Proton Vpn Blog
- – Protocol State Fuzzing Of An Openvpn
- – Openvpn Working With Tcp Not With Udp
- – Best Vpn Security Protocols - Vpn Protocols -...
- – Introduction To Vpns
- – Openvpn Vs. Ikev2 Vs. L2tp: Which Vpn Protoc...
- – Vpn Server Protocol Or Trick Work In Iran
- – Understanding Vpn Protocols: Which One Is Best?
Openvpn(8): Secure Ip Tunnel Daemon - Linux Man Page
It is possible to use Open, VPN freely since it is open source, which suggests you are free to use it if you follow the conditions in the software application license arrangement. While the code is totally free, it's worth pointing out that it needs a lot of manual configuration (i.
In most cases, you will benefit from the free, non-proprietary nature of the procedure while paying to use it through a productized VPN service like Express, VPN or Nord, VPN. But what is it great for if it's not super-safe? You may have seen that your VPN breaks this out as two protocols: Open, VPN UDP and Open, VPN TCP.
What Is Openvpn? - Proton Vpn Blog
A key function of Open, VPN is that it is really versatile and one version can differ from another. Your VPN service provider may utilize a various version than what's being utilized by another company.
When they discover a bug, they repair it and they likewise keep attempting to include brand-new functions to it. This is the main reason behind the versatility of Open, VPN.There are a variety of ciphers supported by Open, VPN. As a standard, Open, VPN executes 256-bit encryption, although it's not obligatory (you might have seen some VPN providers using Open, VPN with AES-128 bit file encryption).
Protocol State Fuzzing Of An Openvpn
So no matter how your VPN supplier might select to set up their servers and connectivity, Open, VPN will be appropriate for them. There are some protocols that are device-dependent. For example, PPTP does not work on Mac computers. Open, VPN, on the other hand, can run on Windows, Mac, Android, i, OS, Linux, and other platforms.
This suggests while the government might not understand what you're doing, the VPN company knows when you logged in and when you logged out. And this details can, if required, be handed over to the government.
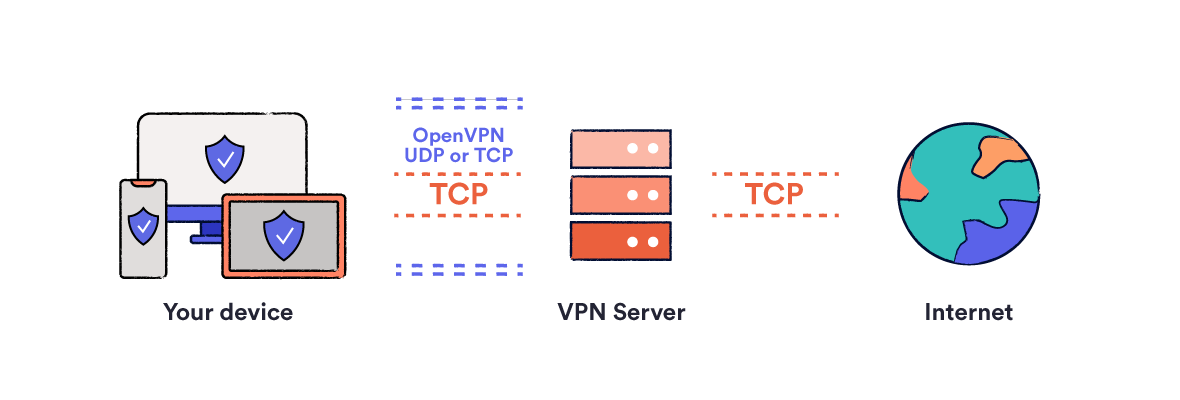
Openvpn Working With Tcp Not With Udp
I checked 30+ VPNs and found the best ones that use Open, VPN. It comes with the procedure pre-configured along with its other security procedure choices.
This has produced a neighborhood of VPN protocol developers and users who constantly test, update, and enhance the protocol. Like any VPN, Open, VPN.
Best Vpn Security Protocols - Vpn Protocols - Openvpn
Premium VPNs, like Express, VPN, already have the protocol preconfigured. Unless you are experienced in manual configuration, working with Open, VPN can be really lengthy and complex.
For circumstances, the settings can be altered and personalized depending on your preference. The same goes for when you use Open, VPN by means of a VPN supplier. Open, VPN works differently based on the settings and configurations. that constantly updates Open, VPN. This community works to update, improve, and repair the protocol when needed, which might change how it runs as updates roll out.
Introduction To Vpns
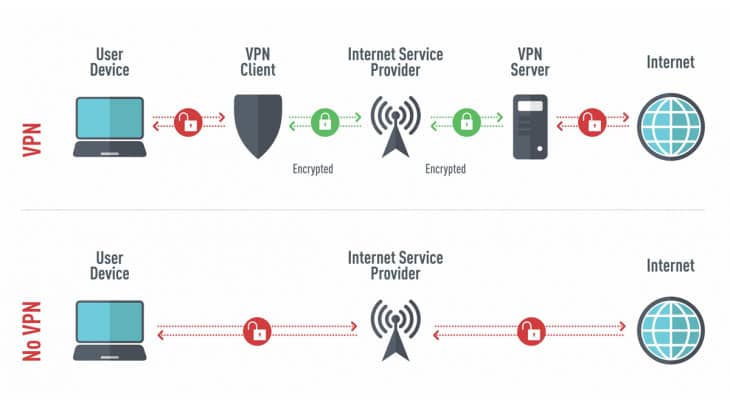
SSL/TLS protocols share the secrets to encode and decode info sent between devices. This is where your information is secured. The most typical file encryption techniques are Cha, Cha and AES 256-bit encryption. These ciphers use keys the elements that "unlock" encrypted messages, for example, 256 0s and 1sts, making them really challenging to translate.
This protocol manages how your information is sent and guarantees everything sends in the proper order, so there's no jumbling of info. It does this by way of a corrective mechanism within the procedure. TCP produces a really reliable method to send out info. Since it processes your information really intently, it can result in slower web speeds.
Openvpn Vs. Ikev2 Vs. L2tp: Which Vpn Protocol Is The ...
VPNs like Cyber, Ghost offer Open, VPN on both Android and i, OS. Since Open, VPN is so popular, some servers and systems look for this procedure and block it. Using Open, VPN with a VPN can assist you prevent this. For example, Express, VPN provides Open, VPN among its procedure choices and can navigate these blocks most of the time.
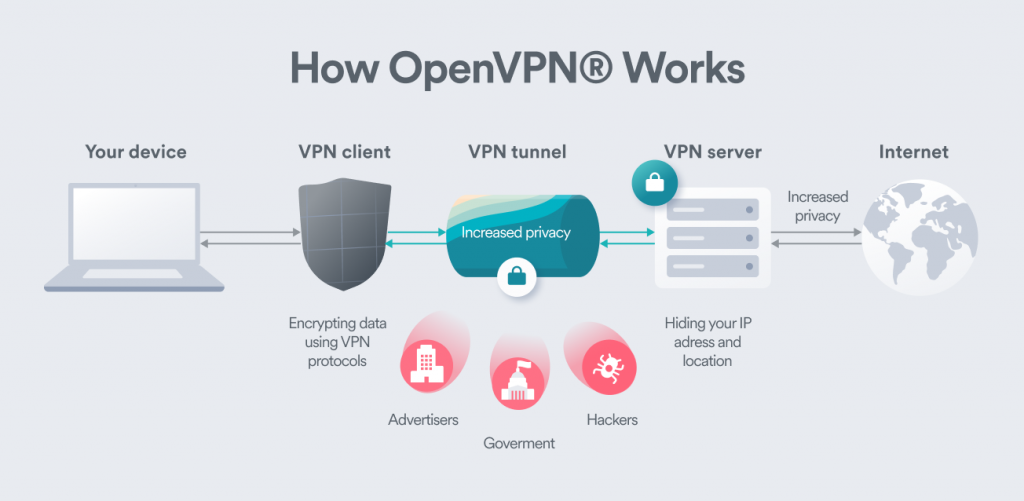
Open, VPN is even generally considered safe from spying by the NSA (United States National Security Firm), which has sophisticated techniques and a large spending plan, which is very remarkable. as an open-source procedure, making it more credible. When a huge company manages a procedure, you have to trust it not to share your info with government companies or other organizations.
Vpn Server Protocol Or Trick Work In Iran
Open, VPN uses a list of recommendations to improve security after installation for that really function. by ensuring Open, VPN is configured correctly. I advise using a premier VPN, such as Express, VPN, so you can rely on that your information stays private. I recommend Express, VPN as Open, VPN comes pre-configured, and it won't compromise your speed.
Go to settings and select Open, VPN. Then, select TCP (more safe and secure) or UDP (much better speeds). You can now search the web, play video games, stream videos, and more with confidence that your information is kept private. Tech-savvy users can do so reasonably quickly, but there is still space for error in this procedure, and any errors could be challenging to fix.
Understanding Vpn Protocols: Which One Is Best?
I used ipleak. It would be unreadable even if someone were to get their hands on your data.
Table of Contents
- – Openvpn(8): Secure Ip Tunnel Daemon - Linux Man...
- – What Is Openvpn? - Proton Vpn Blog
- – Protocol State Fuzzing Of An Openvpn
- – Openvpn Working With Tcp Not With Udp
- – Best Vpn Security Protocols - Vpn Protocols -...
- – Introduction To Vpns
- – Openvpn Vs. Ikev2 Vs. L2tp: Which Vpn Protoc...
- – Vpn Server Protocol Or Trick Work In Iran
- – Understanding Vpn Protocols: Which One Is Best?
Latest Posts
The 5 Best Business Vpn To Secure Your Team In 2023
The Best Free Vpn For Android
How To Troubleshoot Common Issues With Avg Secure Vpn
More
Latest Posts
The 5 Best Business Vpn To Secure Your Team In 2023
The Best Free Vpn For Android
How To Troubleshoot Common Issues With Avg Secure Vpn